On Dec. 27 at the 35th Annual Chaos Communication Congress (35C3) event, three individuals from a startup called Wallet Fail allegedly hacked the most popular hardware wallets and revealed their secrets on stage. According to Trezor, however, the hackers at 35C3 did not follow the standard responsible disclosure protocol and Ledger Wallet developers claim the Wallet Fail team only gave the impression of critical vulnerabilities, emphasizing that this was “not the case.”
Also Read: Judge Denies Craig Wright’s Motion to Dismiss Billion-Dollar Bitcoin Lawsuit
A Startup Called Wallet Fail Claims to Have Cracked Cryptocurrency Hardware Wallets
The European Chaos Computer Club hosts a yearly event called the 35th Annual Chaos Communication Congress, a conference that gathers hackers, computer scientists, and security experts. This year at 35C3, attendees saw an hour-long demonstration from a team called Wallet Fail, a group that believes it can break into any cryptocurrency hardware device including top brands like Trezor and Ledger. Wallet Fail presented vulnerabilities that can be fixed in a firmware upgrade, but they claim to have also found issues with the microcontrollers and the bugs would “require a new hardware revision.”
Some of the attacks shown on stage included various software attacks. Wallet Fail showed a slideshow of pictures exposing private information when the device was flash booted. Other attacks seemingly showed severe weaknesses within the supply chain, evil maid attacks, side channel assaults, and other types of social engineering techniques. The video demonstrates cracking the hardware wallet’s proprietary bootloader protection, bypassing microcontrollers, and using web interface glitches to interact with the wallet. In one part of the demonstration video, Wallet Fail flashed a Ledger Nano S device and boot-loaded the old school Snake game that was once installed on Nokia feature phones. After the hour-long demo, the developers uploaded the 35C3 video to the startup’s Wallet.fail website.

Trezor and Ledger Wallet Respond to Vulnerability Accusations
After the website published the video and the 35C3 event came to an end, two of the most popular hardware wallet manufacturers responded to the claims made by Wallet Fail. The CTO of Satoshi Labs, Pavol Rusnak, told his Twitter followers his company was not informed through Trezor’s responsible disclosure program and learned about the vulnerabilities “from the stage.” “We need to take some time to fix these and we’ll be addressing them via a firmware update at the end of January,” Rusnak emphasized on Twitter. According to the Satoshi Labs CTO, he attended the 35C3 conference this year and saw the demo first-hand.
Trezor also responded to the video demo and tweeted:
Please keep in mind that this is a physical vulnerability. An attacker would need physical access to your device, specifically to the board — breaking the case. If you have physical control over your Trezor, you can keep on using it, and this vulnerability is not a threat to you.
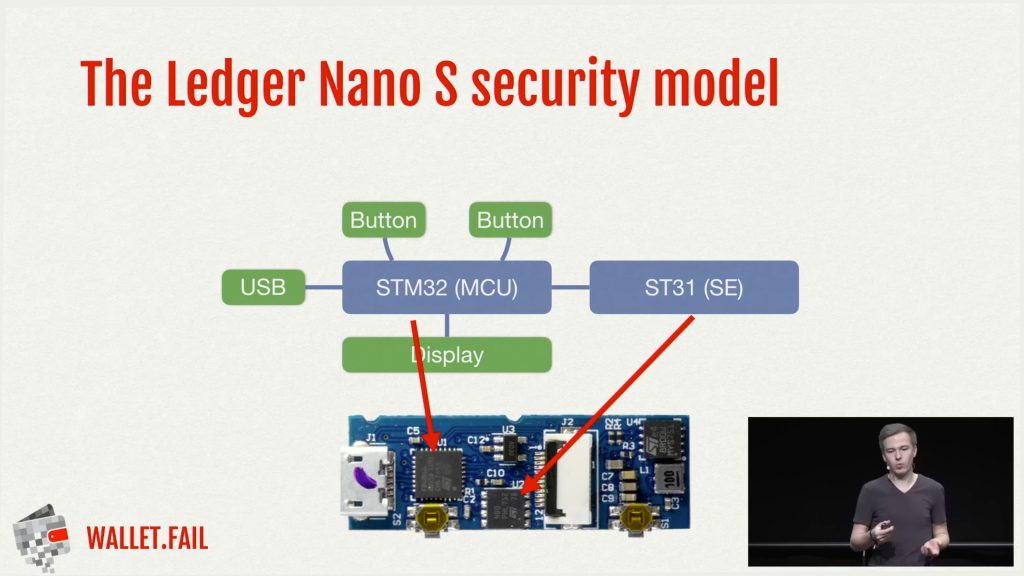
The Ledger Wallet team headquartered in France also responded to Wallet Fail’s accusations. According to Ledger, the Wallet Fail team presented a total of three attack vectors which had given the audience the impression of “critical vulnerabilities.” However, the Ledger developers state that “this is not the case” and users should not worry about securing assets on Ledger devices.
“In particular they did not succeed to extract any seed nor PIN on a stolen device. Every sensitive assets stored on the Secure Element remain secure,” detailed the Ledger team’s blog post on Friday.
Ledger continued:
[Our] responsible disclosure is the best practice to follow in order to protect the end users while improving our products’ security.
Hardware Wallet Manufacturers’ Uphill Battle
This isn’t the first time hardware wallet manufacturers have had to deal with wallet hackers who claim they can compromise any device. Back in the Summer of 2017 at Def Con 25 in Las Vegas, attendees saw an exhibit which allegedly disclosed vulnerabilities in popular cryptocurrency hardware wallets. Last March a teenager told Ars Technica he created code that could find a “backdoor” in Ledger devices. However, again Ledger Wallet told the public that 15-year-old Saleem Rashid’s published post on certain vectors was “not critical” and the attacks “cannot extract the private keys or the seed.”
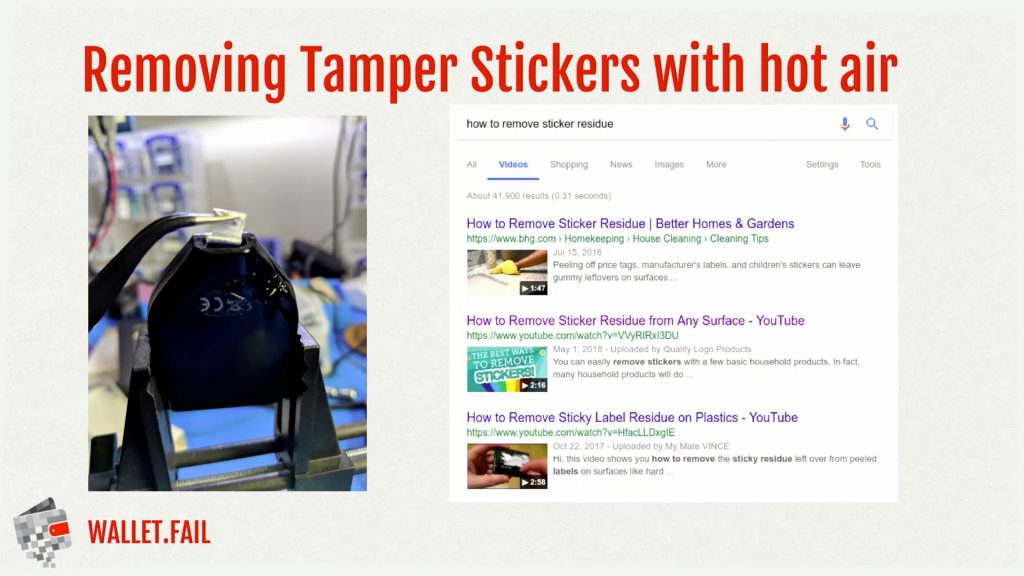
As usual, most of the vulnerabilities have been taken with a grain of salt because a great majority of attacks shown over the years require stealing the physical device itself and remote attacks still seem implausible. The companies who responded to Wallet Fail’s recent demo stressed that people should use a secondary passphrase. A few cryptocurrency veterans also stressed on social media the importance of using a PIN with hardware devices.
What do you think about the alleged hardware wallet vulnerabilities presented at the Annual Chaos Communication Congress? Let us know what you think about this subject in the comments section below.
Images via Wallet Fail’s slide show, 35C3, Shutterstock, and Pixabay.
Need to calculate your bitcoin holdings? Check our tools section.
The post These Developers Claim They Can Crack Any Hardware Wallet appeared first on Bitcoin News.
Powered by WPeMatico

